File integrity monitoring что это
What Is FIM (File Integrity Monitoring)?
File integrity monitoring (FIM) exists because change is prolific in organizations’ IT environments. Hardware assets change. Software programs change. Configuration states change. Some of these modifications are authorized insofar as they occur during a patch cycle; some cause concern by their unexpected nature.
Organizations commonly respond to such dynamism by investing in asset discovery and secure configuration management (SCM). These foundational controls allow companies to track their devices and monitor those products’ configurations. Even so, companies are left with an important challenge: reconciling change in important files. For that challenge, enterprises turn to FIM.
What Exactly is File Integrity Monitoring?
File integrity monitoring was invented in part by Tripwire founder Gene Kim and went on to become a security control that many organizations build their cybersecurity programs around. The term “file integrity monitoring” was widely popularized by the PCI standard.
FIM is a technology that monitors and detects changes in files that may indicate a cyberattack. Unfortunately, for many organizations, FIM mostly means noise: too many changes, no context around these changes, and very little insight into whether a change actually poses a risk. FIM is a critical security control, but it must provide sufficient insight and actionable intelligence.
Otherwise known as change monitoring, file integrity monitoring involves examining files to see if and when they change, how they change, who changed them, and what can be done to restore those files if those modifications are unauthorized.
Companies can leverage the control to supervise static files for suspicious modifications such as adjustments to their IP stack and email client configuration. As such, FIM is useful for detecting malware as well as achieving compliance with regulations like the Payment Card Industry Data Security Standard (PCI DSS).
3 Advantages of Running a Successful File Integrity Monitoring Program
How File Integrity Monitoring Works (in 5 Steps)
There are five steps to file integrity monitoring:
4 Things to Look for When Assessing File Integrity Monitoring Tools
To complement the phases described above, organizations should look for additional features in their file integrity monitoring solution. That functionality should include, for example, a lightweight agent that can toggle “on” and “off” and can accommodate additional functions when necessary. The solution should also come with total control over a FIM policy. Such visibility should incorporate:
File Integrity Monitoring with Tripwire
Tripwire’s file integrity monitoring solution focuses on adding business context to data for all changes that occur in an organization’s environment. As such, it provides IT and security teams with real-time intelligence that they can use to identify incidents that are of real concern. It also helps personnel learn the who, what, when, and how of a change, data which they can use to validate planned modifications.
File integrity monitoring is just one of the foundational controls for which organizations should look when purchasing a new solution. Here are three core components of a FIM solution:
Detecting Change
Every security breach begins with a single change. A small alteration to one file can expose your whole network to a potential attack. File integrity monitoring, in its simplest sense, is about keeping track of change from an established baseline and alerting you to any unexpected change that may represent a security risk or a compromise in regulatory compliance. Whether it’s a phishing scam, DDoS attack, malware, ransomware or insider threat, your FIM solution should alert you right away anytime a cybercriminal is penetrating your system.
Comparing Against a Secure Baseline
In order to know which file changes are relevant to your security, you must first establish an authoritative data integrity baseline. A FIM solution like Tripwire® File Integrity Manager will capture your system’s configuration baseline and deliver the “who, what and when” details of each relevant file change—without bogging you down in notifications about routine changes.
Please download the white paper FIM Isn’t Just for Files Anymore for information on other core security measures of interest.
Video: Watch File Integrity Monitoring in Action
Share This Post
About David Bisson
David Bisson has contributed 1,762 post to The State of Security.
Compare baselines using File Integrity Monitoring (FIM)
Azure Security Center and Azure Defender are now called Microsoft Defender for Cloud. We’ve also renamed Azure Defender plans to Microsoft Defender plans. For example, Azure Defender for Storage is now Microsoft Defender for Storage.
File Integrity Monitoring (FIM) informs you when changes occur to sensitive areas in your resources, so you can investigate and address unauthorized activity. FIM monitors Windows files, Windows registries, and Linux files.
This topic explains how to enable FIM on the files and registries. For more information about FIM, see File Integrity Monitoring in Microsoft Defender for Cloud.
Why use FIM?
Operating system, applications, and associated configurations control the behavior and security state of your resources. Therefore, attackers target the files that control your resources, in order to overtake a resource’s operating system and/or execute activities without being detected.
In fact, many regulatory compliance standards such as PCI-DSS & ISO 17799 require implementing FIM controls.
Enable built-in recursive registry checks
The FIM registry hive defaults provide a convenient way to monitor recursive changes within common security areas. For example, an adversary may configure a script to execute in LOCAL_SYSTEM context by configuring an execution at startup or shutdown. To monitor changes of this type, enable the built-in check.
Recursive checks apply only to recommended security hives and not to custom registry paths.
Add a custom registry check
FIM baselines start by identifying characteristics of a known-good state for the operating system and supporting application. For this example, we will focus on the password policy configurations for Windows Server 2008 and higher.
| Policy Name | Registry Setting |
|---|---|
| Domain controller: Refuse machine account password changes | MACHINE\System\CurrentControlSet\Services \Netlogon\Parameters\RefusePasswordChange |
| Domain member: Digitally encrypt or sign secure channel data (always) | MACHINE\System\CurrentControlSet\Services \Netlogon\Parameters\RequireSignOrSeal |
| Domain member: Digitally encrypt secure channel data (when possible) | MACHINE\System\CurrentControlSet\Services \Netlogon\Parameters\SealSecureChannel |
| Domain member: Digitally sign secure channel data (when possible) | MACHINE\System\CurrentControlSet\Services \Netlogon\Parameters\SignSecureChannel |
| Domain member: Disable machine account password changes | MACHINE\System\CurrentControlSet\Services \Netlogon\Parameters\DisablePasswordChange |
| Domain member: Maximum machine account password age | MACHINE\System\CurrentControlSet\Services \Netlogon\Parameters\MaximumPasswordAge |
| Domain member: Require strong (Windows 2000 or later) session key | MACHINE\System\CurrentControlSet\Services \Netlogon\Parameters\RequireStrongKey |
| Network security: Restrict NTLM: NTLM authentication in this domain | MACHINE\System\CurrentControlSet\Services \Netlogon\Parameters\RestrictNTLMInDomain |
| Network security: Restrict NTLM: Add server exceptions in this domain | MACHINE\System\CurrentControlSet\Services \Netlogon\Parameters\DCAllowedNTLMServers |
| Network security: Restrict NTLM: Audit NTLM authentication in this domain | MACHINE\System\CurrentControlSet\Services \Netlogon\Parameters\AuditNTLMInDomain |
To learn more about registry settings supported by various operating system versions, refer to the Group Policy Settings reference spreadsheet.
To configure FIM to monitor registry baselines:
In the Add Windows Registry for Change Tracking window, in the Windows Registry Key text box, enter the following registry key:
Track changes to Windows files
In the Add Windows File for Change Tracking window, in the Enter path text box, enter the folder which contains the files that you want to track. In the example in the following figure, Contoso Web App resides in the D:\ drive within the ContosWebApp folder structure.
Create a custom Windows file entry by providing a name of the setting class, enabling recursion, and specifying the top folder with a wildcard (*) suffix.
Retrieve change data
File Integrity Monitoring data resides within the Azure Log Analytics / ConfigurationChange table set.
Set a time range to retrieve a summary of changes by resource. In the following example, we are retrieving all changes in the last fourteen days in the categories of registry and files:
| where ConfigChangeType in (‘Registry’, ‘Files’)
| summarize count() by Computer, ConfigChangeType
To view details of the registry changes:
| where ConfigChangeType in (‘Registry’)
Reports can be exported to CSV for archival and/or channeled to a Power BI report.
Как настроить File Integrity Monitoring (FIM) с использованием osquery в Linux
Osquery – это операционная система с открытым исходным кодом, мониторинга и аналитики.
Созданный Facebook, она предоставляет операционную систему как высокопроизводительную реляционную базу данных, которая может работать с использованием запросов на основе SQL.
Osquery – это многоплатформенное программное обеспечение, которое может быть установлено на Linux, Windows, MacOS и FreeBSD.
Она позволяет нам исследовать все профили, производительность, безопасность и т. д. этих операционных систем, используя запросы на основе SQL.
В этом уроке мы покажем вам, как настроить File Integrity Monitoring (FIM) с osquery.
Мы будем использовать операционные системы Linux Ubuntu 18.04 и CentOS 7.
Предпосылки
Шаг 1 – Установите osquery на Linux Server
Osquery предоставляет собственный репозиторий для установки на платформе, и первым шагом, который мы собираемся сделать, является установка пакета osquery из официального репозитория osquery.
На Ubuntu
Добавьте в систему ключ osquery.
Добавьте репозиторий osquery и установите пакет.
На CentOS
Добавьте в систему ключ osquery.
Добавьте и включите репозиторий osquery и установите пакет.
Подождите, пока все пакеты будут установлены.
Если вы получите сообщение об ошибке команды yum-config-manager:
Установите пакет «yum-utils».
Шаг 2 – Включите обработку Syslog в osquery
Osquery предоставляет функции для чтения или использования системных журналов на Apple MacOS с использованием системного журнала Apple (ASL), а для Linux используется syslog.
На этом этапе мы включим syslog для osquery через rsyslog.
На Ubuntu
Установите пакет rsyslog, используя команду apt, приведенную ниже:
На CentOS
Установите пакет rsyslog с помощью команды yum :
По завершении установки перейдите в каталог ‘/etc/rsyslog.d’ и создайте новый файл конфигурации osquery.conf.
Вставьте следующую конфигурацию:
Сохраните и закройте файл.
Шаг 3 – Основная настройка osquery
Конфигурационный файл по умолчанию – это «osquery.conf», обычно находящийся в каталоге «/etc/osquery».
Имеются образцы конфигурации osquery ‘/usr/share/osquery/osquery.conf’ и образец конфигурации пакетов osquery.
На этом этапе мы узнаем о компонентах конфигурации osquery, создадим настраиваемую конфигурацию osquery и затем развернем osqueryd в качестве службы.
Конфигурация osquery, отформатированная как файл JSON, содержит спецификации конфигурации osquery, описанные ниже.
Перейдите в каталог «/etc/osquery» и создайте новую конфигурацию «osquery.conf».
Вставьте в этот файл следующую конфигурацию:
Сохраните и закройте.
Мы используем «filesystem» в качестве плагина конфигурации и регистратора.
Определите путь регистрации в каталоге ‘/ var / log / osquery’.
Включите syslog в файл ‘/ var / syslog / syslog_pipe’.
В планировщике мы определяем три запроса для проверки crontab, системной информации и входа ssh.
Включите пакеты osquery с именем «osquery-monitoring» и упаковывайте файлы, расположенные в каталоге «/ usr / share / osquery / packs».
Теперь запустите службу daemon osqueryd и включите ее для запуска каждый раз при загрузке системы.
И перезагрузите службу rsyslog
На этом завершена основная настройка osquery.
Шаг 4 – Настройка контроля целостности файлов (FIM) используя osquery
Osquery обеспечивает мониторинг целостности файлов в Linux и MacOS Darwin с использованием inotify и FSEvents.
Просто он отслеживает и обнаруживает любые изменения файлов в определенном каталоге с помощью «file_path», а затем сохраняет всю активность в таблице file_events.
На этом этапе мы сконфигурируем osquery для мониторинга важных каталогов, таких как home, ssh и т. д., Tmp и корневой каталог www web, используя пользовательские пакеты FIM.
Перейдите в каталог ‘/usr/share/osquery/packs’ и создайте новый файл конфигурации ff.conf.
Вставьте в него содержимое ниже:
Сохраните и закройте файл.
Вернитесь в каталог конфигурации «/etc/osquery» и отредактируйте файл osquery.conf.
Добавьте конфигурацию пакетов контроля целостности файла в разделе «packs».
Сохраните и выйдите, а затем перезапустите службу osqueryd.
Продолжайте проверять конфигурационный файл JSON с помощью JSON linter ‘http://jsonlint.com/’ и убедитесь, что ошибок нет.
Шаг 5 – Тестирование
Мы проверим пакеты контроля целостности файлов, создав новый файл в определенном каталоге «home» и «www».
Перейдите в каталог ‘/var/www/’ и создайте новый файл с именем ‘howtoforge.md’.
Перейдите в каталог «/home/youruser /» и создайте новый файл с именем «hakase-labs.md».
Теперь мы проверим мониторинг всех журналов с помощью интерактивного режима osqueryi в реальном времени и журналов результатов osquery.
osqueryi
Запустите команду osqueryi:
Теперь проверьте все журналы изменений файла в таблице «file_events».
Для глобальных изменений.
Для корневого каталога веб-сайта www.
журнал результатов osqueryd
Перейдите в каталог ‘/var/log/osquery’, и вы получите файл ‘osqueryd.results.log’.
Отфильтруйте журналы osquery с помощью команды grep.
File integrity monitoring in Microsoft Defender for Cloud
Azure Security Center and Azure Defender are now called Microsoft Defender for Cloud. We’ve also renamed Azure Defender plans to Microsoft Defender plans. For example, Azure Defender for Storage is now Microsoft Defender for Storage.
Learn how to configure file integrity monitoring (FIM) in Microsoft Defender for Cloud using this walkthrough.
Availability
What is FIM in Defender for Cloud?
File integrity monitoring (FIM), also known as change monitoring, examines operating system files, Windows registries, application software, Linux system files, and more, for changes that might indicate an attack.
Defender for Cloud recommends entities to monitor with FIM, and you can also define your own FIM policies or entities to monitor. FIM informs you about suspicious activity such as:
In this tutorial you’ll learn how to:
How does FIM work?
The Log Analytics agent uploads data to the Log Analytics workspace. By comparing the current state of these items with the state during the previous scan, FIM notifies you if suspicious modifications have been made.
FIM uses the Azure Change Tracking solution to track and identify changes in your environment. When file integrity monitoring is enabled, you have a Change Tracking resource of type Solution. For data collection frequency details, see Change Tracking data collection details.
If you remove the Change Tracking resource, you will also disable the file integrity monitoring feature in Defender for Cloud.
Which files should I monitor?
When choosing which files to monitor, consider the files that are critical for your system and applications. Monitor files that you don’t expect to change without planning. If you choose files that are frequently changed by applications or operating system (such as log files and text files) it’ll create a lot of noise, making it difficult to identify an attack.
Defender for Cloud provides the following list of recommended items to monitor based on known attack patterns.
| Linux files | Windows files | Windows registry keys (HKLM = HKEY_LOCAL_MACHINE) |
|---|---|---|
| /bin/login | C:\autoexec.bat | HKLM\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllRemoveSignedDataMsg |
| /bin/passwd | C:\boot.ini | HKLM\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllRemoveSignedDataMsg |
| /etc/*.conf | C:\config.sys | HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\SYSTEM.ini\boot |
| /usr/bin | C:\Windows\system.ini | HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows |
| /usr/sbin | C:\Windows\win.ini | HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| /bin | C:\Windows\regedit.exe | HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders |
| /sbin | C:\Windows\System32\userinit.exe | HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders |
| /boot | C:\Windows\explorer.exe | HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| /usr/local/bin | C:\Program Files\Microsoft Security Client\msseces.exe | HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| /usr/local/sbin | HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx | |
| /opt/bin | HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices | |
| /opt/sbin | HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce | |
| /etc/crontab | HKLM\SOFTWARE\WOW6432Node\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllRemoveSignedDataMsg | |
| /etc/init.d | HKLM\SOFTWARE\WOW6432Node\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllRemoveSignedDataMsg | |
| /etc/cron.hourly | HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\IniFileMapping\system.ini\boot | |
| /etc/cron.daily | HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Windows | |
| /etc/cron.weekly | HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Winlogon | |
| /etc/cron.monthly | HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders | |
| HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders | ||
| HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run | ||
| HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce | ||
| HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnceEx | ||
| HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunServices | ||
| HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunServicesOnce | ||
| HKLM\SYSTEM\CurrentControlSet\Control\hivelist | ||
| HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\KnownDLLs | ||
| HKLM\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile | ||
| HKLM\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\PublicProfile | ||
| HKLM\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile |
Enable file integrity monitoring
FIM is only available from Defender for Cloud’s pages in the Azure portal. There is currently no REST API for working with FIM.
From the Workload protections dashboard’s Advanced protection area, select File integrity monitoring.
The File integrity monitoring configuration page opens.
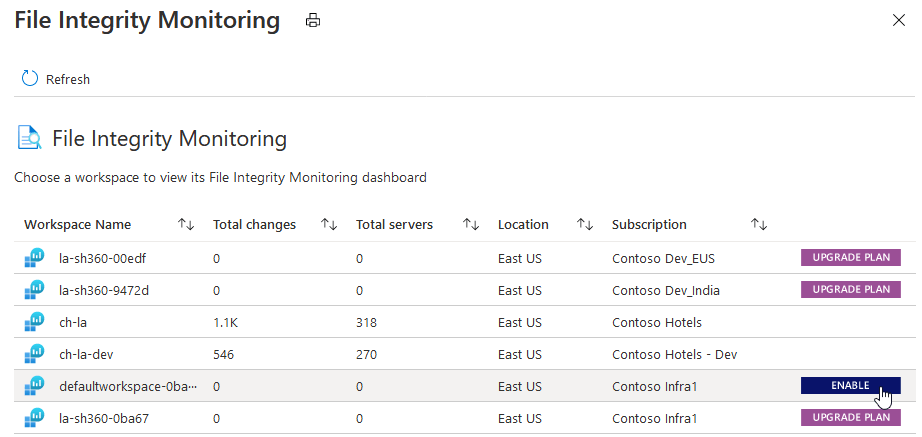
The following information is provided for each workspace:
Access and view the status and settings of each workspace


If there’s no enable or upgrade button, and the space is blank, it means that FIM is already enabled on the workspace.
Select ENABLE. The details of the workspace including the number of Windows and Linux machines under the workspace is shown.
The recommended settings for Windows and Linux are also listed. Expand Windows files, Registry, and Linux files to see the full list of recommended items.
Clear the checkboxes for any recommended entities you do not want to be monitored by FIM.
Select Apply file integrity monitoring to enable FIM.
You can change the settings at any time. See Edit monitored entities below to learn more.
Audit monitored workspaces
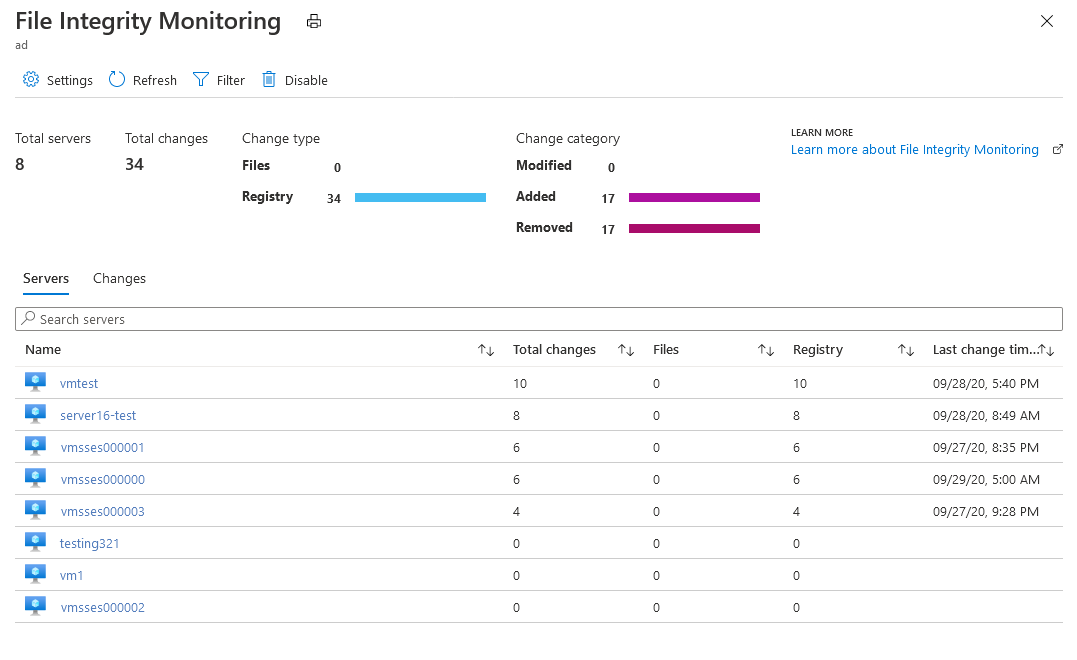
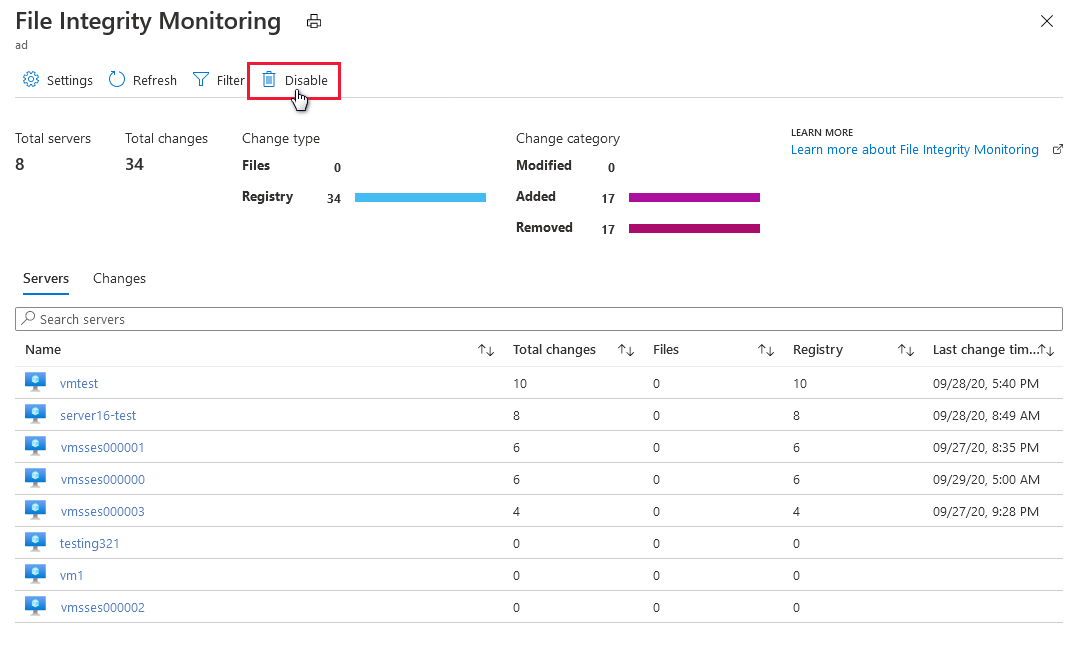
The File integrity monitoring dashboard displays for workspaces where FIM is enabled. The FIM dashboard opens after you enable FIM on a workspace or when you select a workspace in the file integrity monitoring window that already has FIM enabled.
The FIM dashboard for a workspace displays the following details:
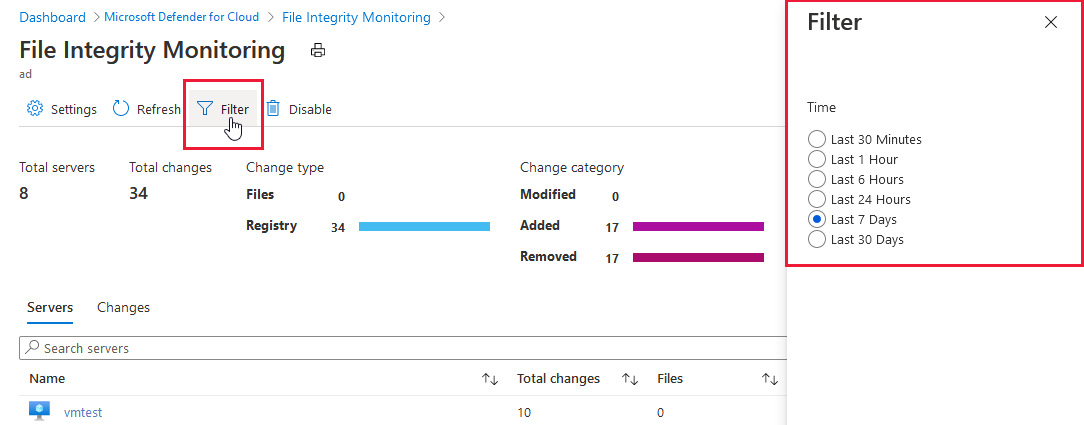
Select Filter at the top of the dashboard to change the time period for which changes are shown.
The Servers tab lists the machines reporting to this workspace. For each machine, the dashboard lists:
When you select a machine, the query appears along with the results that identify the changes made during the selected time period for the machine. You can expand a change for more information.
The Changes tab (shown below) lists all changes for the workspace during the selected time period. For each entity that was changed, the dashboard lists the:
Change details opens when you enter a change in the search field or select an entity listed under the Changes tab.
Edit monitored entities
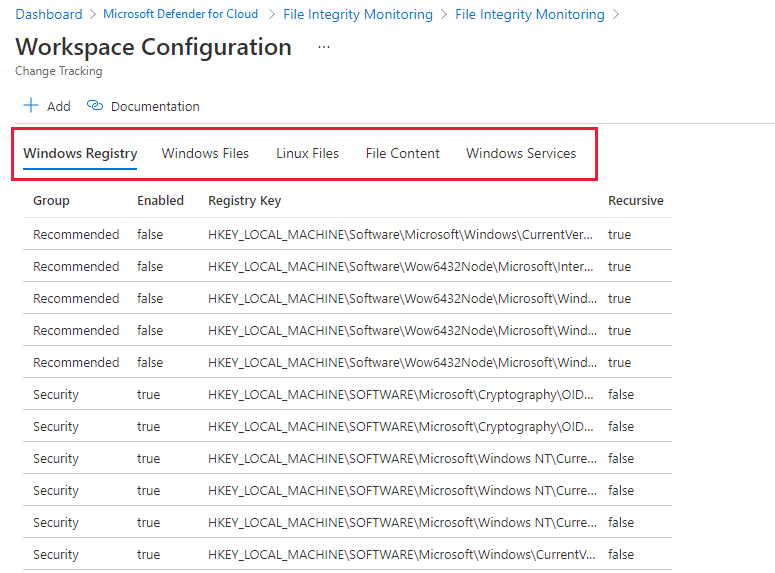
From the File integrity monitoring dashboard for a workspace, select Settings from the toolbar.
Workspace Configuration opens with tabs for each type of element that can be monitored:
Each tab lists the entities that you can edit in that category. For each entity listed, Defender for Cloud identifies whether FIM is enabled (true) or not enabled (false). Edit the entity to enable or disable FIM.
Select an entry from one of the tabs and edit any of the available fields in the Edit for Change Tracking pane. Options include:
Discard or save your changes.
Add a new entity to monitor
From the File integrity monitoring dashboard for a workspace, select Settings from the toolbar.
The Workspace Configuration opens.
One the Workspace Configuration:
Select the tab for the type of entity that you want to add: Windows registry, Windows files, Linux Files, file content, or Windows services.
Select Add.
In this example, we selected Linux Files.
Select Add. Add for Change Tracking opens.
Enter the necessary information and select Save.
Folder and path monitoring using wildcards
Use wildcards to simplify tracking across directories. The following rules apply when you configure folder monitoring using wildcards:
Disable FIM
You can disable FIM. FIM uses the Azure Change Tracking solution to track and identify changes in your environment. By disabling FIM, you remove the Change Tracking solution from selected workspace.
From the File integrity monitoring dashboard for a workspace, select Disable.
Select Remove.
Next steps
In this article, you learned to use file integrity monitoring (FIM) in Defender for Cloud. To learn more about Defender for Cloud, see the following pages: